SSH, Secure SHell is a fantastic piece of software. It can do many many things to help you secure data transfer. Though when entering to the very same servers over and over and over it can be a bit of a hazard having to type in that very same password just as many times. Now you will learn how to skip that part making it so much easier to use not only ssh but other commands like rsync and scp.
SSH, Secure SHell is a fantastic piece of software. It can do many many things to help you secure data transfer. Though when entering to the very same servers over and over and over it can be a bit of a hazard having to type in that very same password just as many times. Now you will learn how to skip that part making it so much easier to use not only ssh but other commands like rsync and scp.
First we need to create a key on our computer from where we want to connect to the server. Older releases of ubuntu need you to specify the command as on the green line, while on newer releases this is the default value and there is no need to specify any parameters:
: ssh-keygen
: ssh-keygen -t rsa
The key created will have a length of 2048 bits for SSH protocol version 2. This is a very secure key length. As it seams (googling the web) it will take many many years in order to be able to crack a key of this length. Though Debian recommends a length of 4096 bits. This is easily done by adding the -b option like this:
ssh-keygen -t rsa -b 4096
Adding more bits makes the key bigger, more CPU used, more battery drain etc… depending on devices used you might consider what’s best for you. Though if it’s a key that you are planning to use on a public server for many a year to come, 4096 is by far the safer choice. When executing the program you will be asked two things
- Where to save the key
- To set a password
Just press enter and choose the default path on the first step. In this way ssh will always know where to find your key,. About setting a password: Just press enter and leave it blank, if not, you’ll be asked to type a password every time you use this key. This is great when you’re entering really secure systems. Keys are always stronger than passwords and adding a password to the key itself helps protect even more against someone stealing your private key. I myself usually don’t use an extra password since I believe my private key are sufficiently safe. Anyway, after executing the command you will have something like this on your screen:
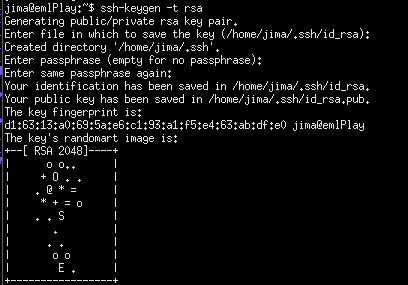
The privet key is yours to keep safe. Never to be given to anyone. The public key however, is to be copied to the server/s you want to connect to.
The key files was saved in your home directory under a folder called “.ssh” and the private key is called “id_rsa” and the public key “id_rsa.pub”.
Here are a couple of options on how to copy your pubic key onto the server.
: ssh-copy-id <user>@<server>
You will be asked for your password on the server and that's it.
OR
: cat ~/.ssh/id_rsa.pub | ssh <user>@<server> 'mkdir -p ~/.ssh && cat >>~/.ssh/authorized_keys'
Create directory if not exist and create/append the key file.
If this doesn’t work make sure the .ssh folder has 700 permissions and that the user and group is the very one you are trying to login with. The authorized_keys file must have 600 permissions.
Cheers
/jima